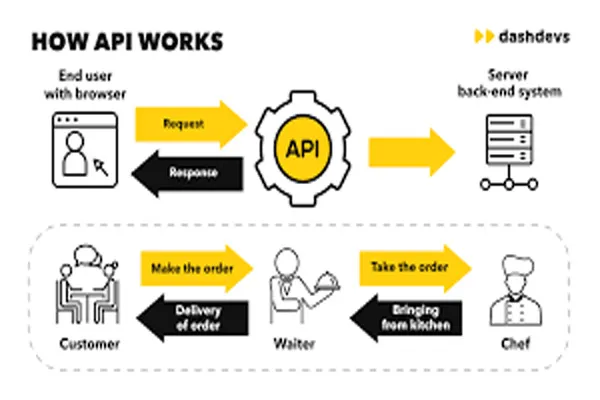
SSL (Secure Sockets Layer) certificates, or their successor TLS (Transport Layer Security) certificates, are essential for establishing secure communication over the internet. They enable encryption between a web server and a web browser, ensuring that any data exchanged remains private and integral.
1. Public-Key Cryptography
SSL certificates rely on public-key cryptography, also known as asymmetric cryptography. This involves two keys:
- Public key: Shared with anyone (it encrypts data).
- Private key: Kept secret by the owner (it decrypts data).
The public key can encrypt data, but only the matching private key can decrypt it. This ensures that even if someone intercepts the encrypted data, they cannot read it without the private key.
2. Certificate Authority (CA)
An SSL certificate is issued by a trusted organization called a Certificate Authority (CA). The CA validates the identity of the entity requesting the certificate (e.g., a website) to ensure that they are who they say they are.
There are different types of SSL certificates, such as:
- Domain Validated (DV) certificates: Basic level, just confirms domain ownership.
- Organization Validated (OV) certificates: Involves validating the organization's identity.
- Extended Validation (EV) certificates: The most rigorous, providing the highest level of trust.
The CA's role is to verify the identity of the certificate requestor and then issue the certificate, which includes the public key and information about the organization.
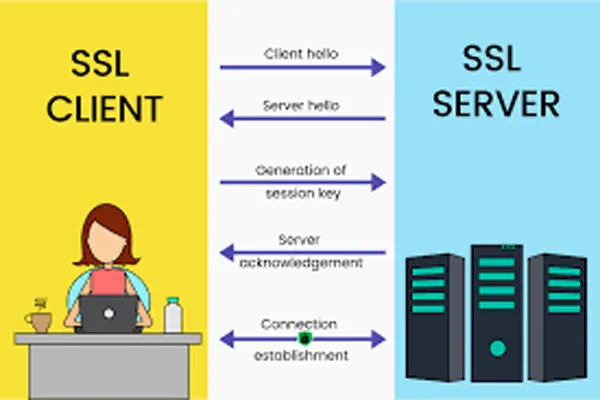
3. The SSL/TLS Handshake
The SSL/TLS handshake is the process that happens when a client (like a web browser) and a server first communicate. Here's a step-by-step overview:
-
Client Hello: The client (browser) sends a request to the server for a secure connection. It includes information such as supported encryption algorithms and a randomly generated number for the session.
-
Server Hello: The server responds by sending its SSL certificate (which includes the server's public key), along with its own random number. The certificate is signed by a trusted CA and assures the client that it’s communicating with the correct server.
-
Authentication: The client verifies the server’s certificate by checking if it's signed by a trusted CA. If the certificate is valid, the client proceeds; if not, a warning will appear to the user.
-
Key Exchange: The client generates a pre-master secret (a shared key for the session) and encrypts it using the server's public key. Only the server can decrypt it with its private key.
-
Session Key Generation: Both the client and server use the pre-master secret, along with the random numbers exchanged earlier, to independently generate the same session key, which will be used to encrypt and decrypt the data during the session.
-
Secure Communication: Once the handshake is complete, both parties have the same session key. All subsequent communication between the client and server is encrypted using this symmetric encryption key, ensuring confidentiality and integrity.
4. Encrypted Data Transfer
After the handshake, the actual data is transferred between the client and server using the symmetric encryption technique. Symmetric encryption uses the same key for both encryption and decryption, which is faster and more efficient than public-key encryption. This ensures that the information, such as credit card numbers or personal details, is protected during transmission.
5. Data Integrity and Authentication
SSL/TLS also ensures data integrity by using cryptographic hash functions. This helps detect if any data has been tampered with during transmission. Additionally, the certificate verifies the identity of the server, ensuring that the client is communicating with the legitimate server and not an imposter.
6. Session Termination
When the session ends, both the client and server can terminate the secure connection by sending a "close_notify" message to each other. This ensures that the connection is closed securely, preventing any further data from being sent over the channel.
Summary of SSL/TLS Benefits:
- Encryption: Protects data during transfer between client and server.
- Authentication: Verifies the identity of the website or server.
- Data Integrity: Ensures that data has not been altered during transmission.
- Trust: SSL certificates, especially EV certificates, display trust indicators like a padlock or the "https://" in the browser address bar.
Why SSL Certificates Are Important:
- Security: They provide encryption, preventing attackers from intercepting or tampering with sensitive data.
- Trust: They help websites gain user trust by confirming that the site is legitimate.
- SEO: Search engines like Google favor HTTPS websites, so SSL certificates can improve search rankings.